
How to automate drift detection in …
Background In this short blog post, we’ll explore how to automate AWS CloudFormation StackSet drift …

Applying AWS CDK Guardrails
Background The AWS Cloud Development Kit (AWS CDK) is an open-source software development framework …

How to Customise the AWS CDK Pipeline
Background Have you ever wanted the power of the AWS CodePipeline mixed with the convenience of the …

Unlocking the Power of AWS CDK: Why It's …
Background At Virtuability, we’re always on the lookout for tools that can enhance our AWS …
Querying AWS CloudTrail Logs with Athena …
Background Over the years, we have helped organisations make sense of their CloudTrail logs when …

Boto3 and Python unittest.mock
I start this post by saying I’m not a professional software developer, I work mainly in IT …

Reduce Cost at Scale with Automated …
Background As organisations continue to grow and with the resulting increases in AWS consumption …
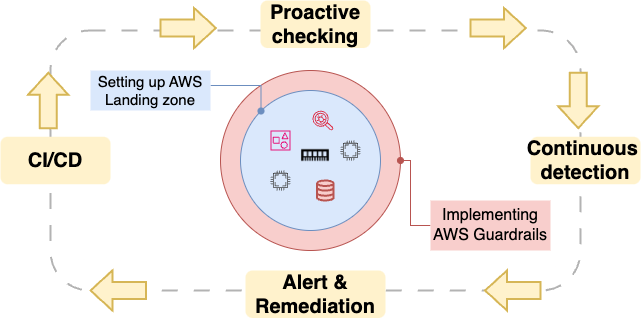
Why organisations should implement AWS …
In a fast-paced cloud environment governance is fundamental, defining standard policies for …

AWS NLB and Client IP Preservation - How …
Have you ever created a Network Load Balancer on AWS, its target group and its target, and some …

Break the rules of virtualization, build …
How often are you deploying a Lambda container image, basically a Lambda running on a Docker image, …

AWS CDK + API Gateway and Integrations. …
I’ve been working with CDK and I think is brilliant, the way it lets you define resources and …

Simply Deploy AWS IAM Identity Center …
With AWS IAM Identity Center, formerly known as AWS Single Sign-On, it became simpler to integrate …

Enable Security Hub in an AWS …
Background In November 2020 AWS announced that Security Hub now integrates with AWS Organizations. …

Use the Raspberry Pi 4 for AWS …
Background With the advent of the Raspberry Pi 4, Pi’s are sufficiently powerful in terms of …

Get started with Ubuntu 20.04 on …
Background With the advent of the Raspberry Pi 4, Pi’s have become quite powerful both in CPU …

Install & run AWS Glue 1.0 and PySpark …
Background It’s much faster to be able to develop and debug AWS Glue / PySpark scripts …

Leveraging Serverless (SAM) with Cognito …
Introduction Using Serverless combined with Cognito can be a great way to eliminate the real estate …

The case for Structured, Contextual Logs
Introduction If correctly composed, logs can be an extremely useful resource to tap into in the …

6 Steps to DevOps
Introduction Why adopt DevOps? IT change can be painful and subject to long lead times in many …

Why Serverless & DevOps makes a (big) …
Background We have recently completed a Serverless & DevOps transformation project with one of …

Moving to Cloud: the Landing Zone
In military terms a Landing Zone is an area where aircraft can land; in effect a base camp from …

Securing Cross-Account AWS API Calls & …
AWS Cross-Account Roles are an excellent way of managing access to a target account (the account in …

Creating a Core Network Foundation in …
For both test and build purposes I often find myself reusing parts of past CloudFormation templates. …

Need a good reason to switch to …
AWS CloudFormation size limits are well-documented in the User Guide. However, this does not make …

Moving to Cloud: Agility
Over the years I have witnessed, proposed and implemented a wide range of AWS use cases; and few of …

Securing AWS API Calls & CLI Access with …
One of the largest concerns of allowing AWS API calls to be made from the outside is issuing an API …